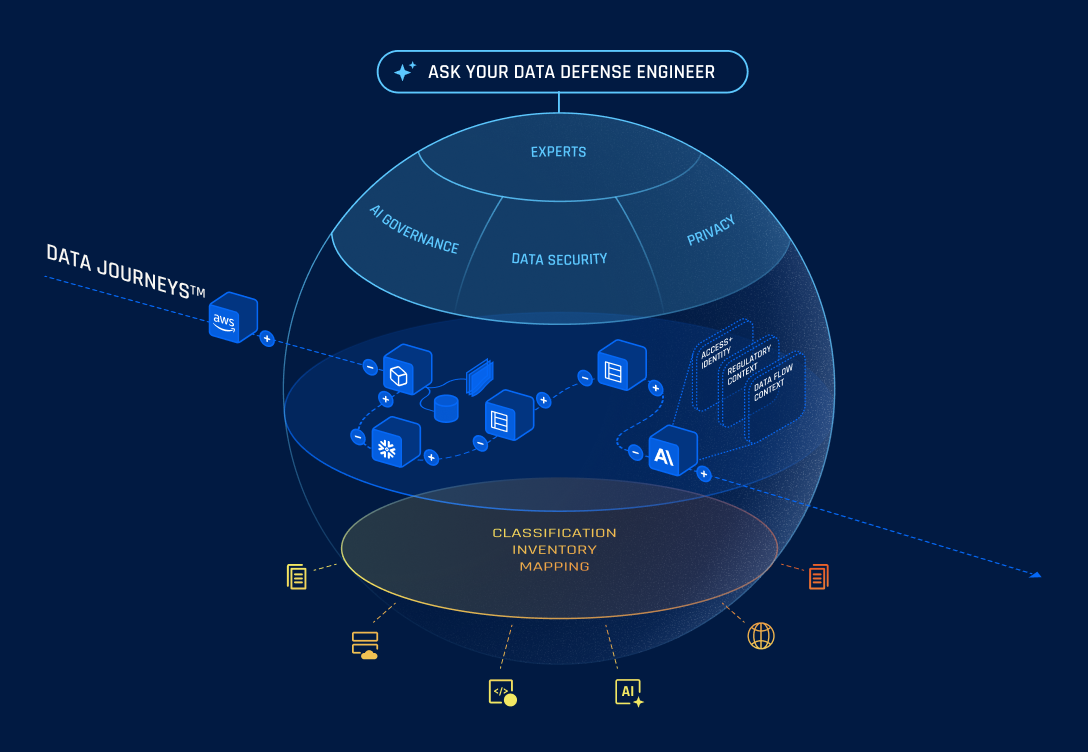
Your Data Defense Engineer.
Code to Cloud.
Superintelligence that tracks every data journey from source code to cloud runtime to AI models to third parties in real-time. Detect violations as they happen while reducing manual effort by 80%.

Trusted by the best
Traditional security tools weren't built for the AI era
35%
data breaches involve "shadow data"
Organizations lose track of data as it flows through code, runtime, and AI models
76%
AI initiatives are not properly secured
Engineering teams deploy AI features daily while security reviews lag by weeks
65%
SaaS apps operate without IT approval
Average company tracks just 108 of 975 cloud services actually in use
AI-era threats demand AI-native expertise
Data Security Expert
Code to Cloud Dynamic DSPM
Continuous monitoring protects data flows from development through production, while real-time detection catches secrets in code, unauthorized access, and policy violations as they happen.
AI Governance Expert
Secure + Govern Shadow / Agentic AI
Illuminate all AI use across your organization, prevent data leaks in training data, prompts, and outputs, and automate compliance with regulations and responsible AI policies.
Privacy Expert
Holistic Global Privacy Compliance
Automated data mapping adapts as systems change, enabling GDPR/CCPA compliance with DSR fulfillment and consent management, while real-time monitoring stops privacy violations before they become breaches.
The complete picture of your data in motion
Powered by Data Journeys™
Ditch legacy tools that miss the action with continuous tracking that follows data flows from source code to AI models, predicting and preventing violations in real-time.
AI-Native Architecture
- Multi-point data visibility across code, runtime, and infrastructure
- Context-aware DSPM spanning clouds, third-party tools, and AI models
- AI-powered risk detection with actionable alerts
Works With Your Existing Stack
- Enhances SIEM with rich data flow context
- Integrates with DevOps for security feedback in existing workflows
- Low false positives with AI that learns your environment
Agentless and Flexible Deployment
- Full SaaS: Managed in secure cloud for rapid deployment
- InHost™: Runs entirely within your VPC for maximum control
- DirectConnect: Private link between your network and platform
Meet the companies who defend data with us


“AI is creating and moving data faster than any team can track. Only AI-native tools like Relyance AI can keep up with the discovery and enforcement loop.”
Chris Bender, CISO


“With Relyance AI, I can be more self sufficient. I don't have to wait for someone to respond to an email or get around to the task I'm asking them. I can go right to the tool and get answers.”
Sheila Jambekar, CPO


"Within 15 minutes of connecting Relyance AI, we had total visibility of our vendors and services. That speed and simplicity changed everything."
Heather Allen, Privacy Officer