Your Data Security Expert.
Code to Cloud.
Discover, classify, and secure sensitive data across your complete data ecosystem. From source code to cloud storage, eliminate blind spots and maintain continuous security posture while your teams move at speed.
Data security challenges that expose you
Traditional DSPM tools miss the action. Here's why.

Data sprawl everywhere
- Traditional DSPM only sees 35% of actual data flows
- Critical data hidden in source code and runtime environments
- Manual discovery can't keep pace with data velocity

Security complexity explosion
- Fragmented tools create dangerous blind spots
- Static scans miss dynamic data transformations
- Point solutions lack complete data journey context

Innovation vs. security tension
- Security reviews slow data initiatives by weeks
- Legacy tools can't handle AI-era data flows
- Manual processes break at cloud scale
Dynamic data security posture management
Transform data security from reactive scanning to proactive protection.
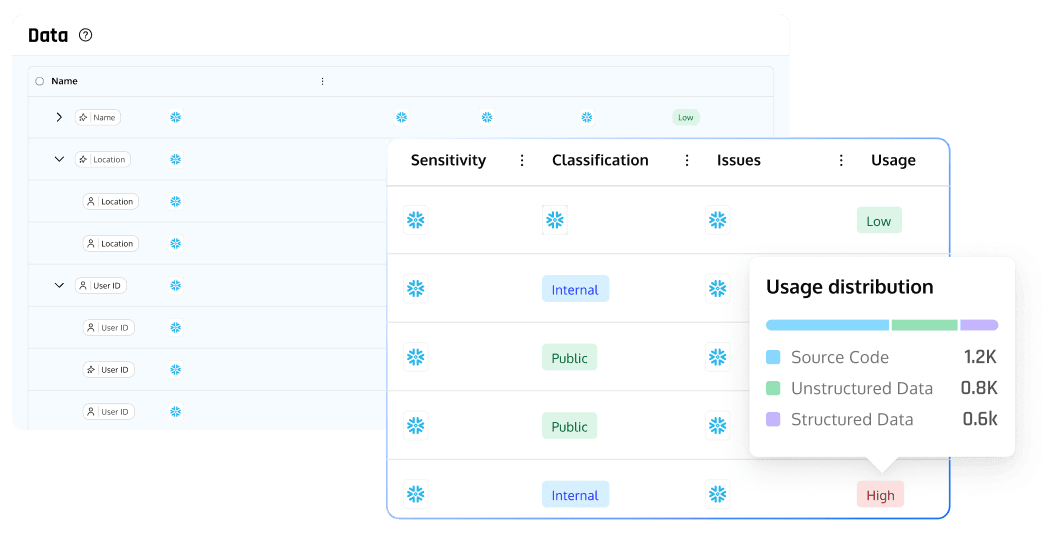
Blind Spot Elimination
Deep visibility and security of sensitive data flowing through source code, cloud runtime, data pipelines, data storage and SaaS applications.
What you get:
- Real-time data discovery across all environments
- Complete visibility from code commit to data storage
- AI-native classification with contextual intelligence
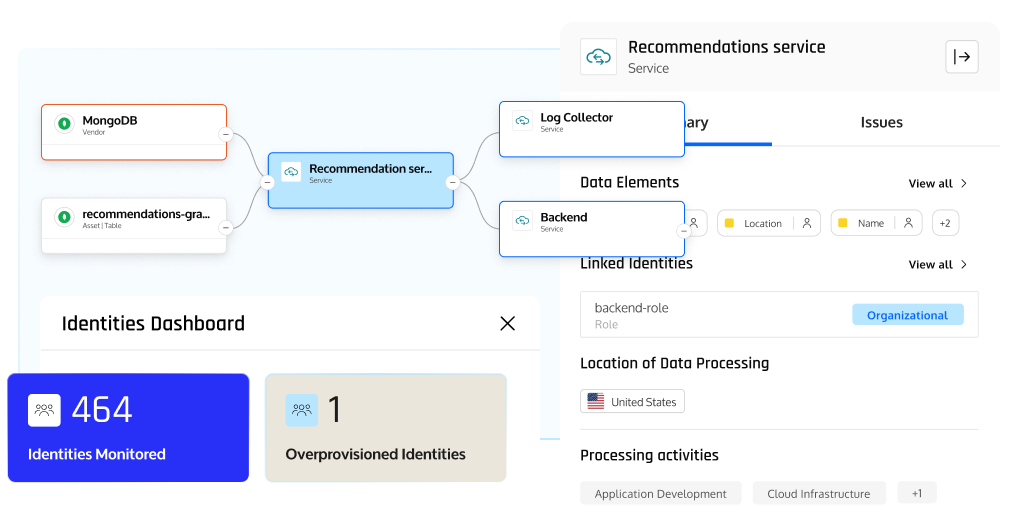
Identity-to-Data Lineage
Map how identities gain access to sensitive data, uncovering permission chains and pinpointing hidden risks.
What you get:
- Instant visibility into identity-to-data access paths
- One-click drill downs from identities, assets, or services
- Risk hot spots flagged for faster remediation
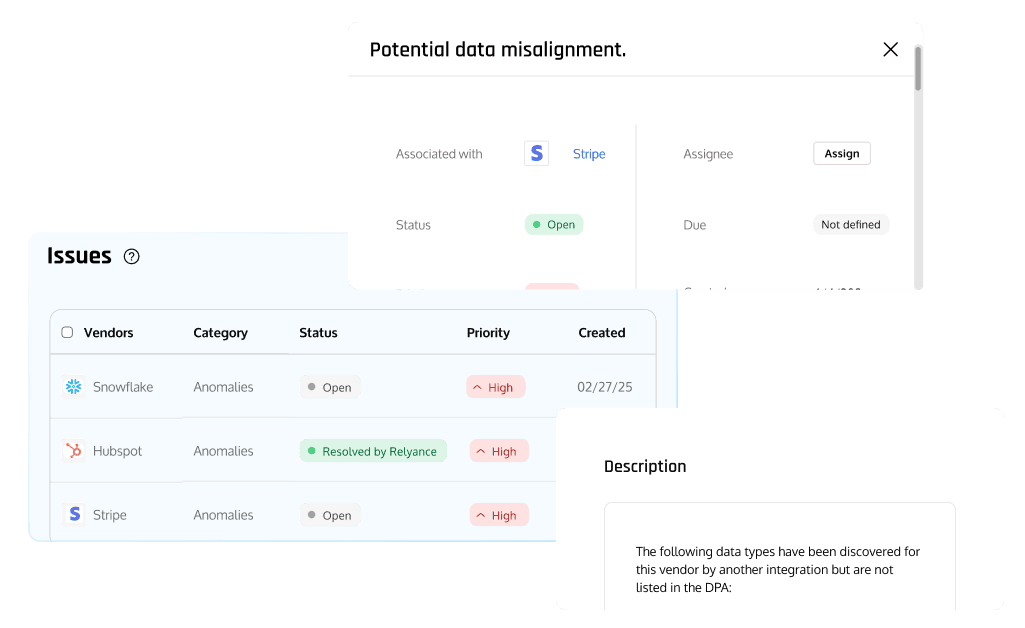
Unified Security and Compliance
Single platform unifying data security, privacy compliance, and AI governance, breaking down silos and streamlining evidence.
What you get:
- Shared data graph for cross-functional visibility
- Continuous compliance checks with regulation-aware controls
- Audit-ready reporting and proof of lawful data use
The complete picture of your data in motion
Ditch legacy tools that miss the action with continuous tracking that follows data flows from source code to AI models, predicting and preventing violations in real-time. Learn about Data Journey breakthrough technology.
Dynamic Data Security for the AI era
Traditional DSPM scans static data. We track complete data lifecycle intelligence.
You may also like

Join Relyance AI at IAPP Global Summit 2026 & meet your 24/7 Data Defense Engineer — from code to cloud

Operationalizing AI Governance in the agentic era









