The End of an Era
There was a time when data security felt almost… predictable.
You could draw boundaries. You could define perimeters. You could point to the systems that held your data and say, “That’s where it lives.”
Those days are over.
AI has upended every assumption we built security on. What used to be a static, rule-based world now behaves like a living organism — adaptive, unpredictable, and often autonomous. AI agents spin up daily, integrating with tools, APIs, and workflows, sometimes with approval, sometimes without. They reason. They act. They learn.
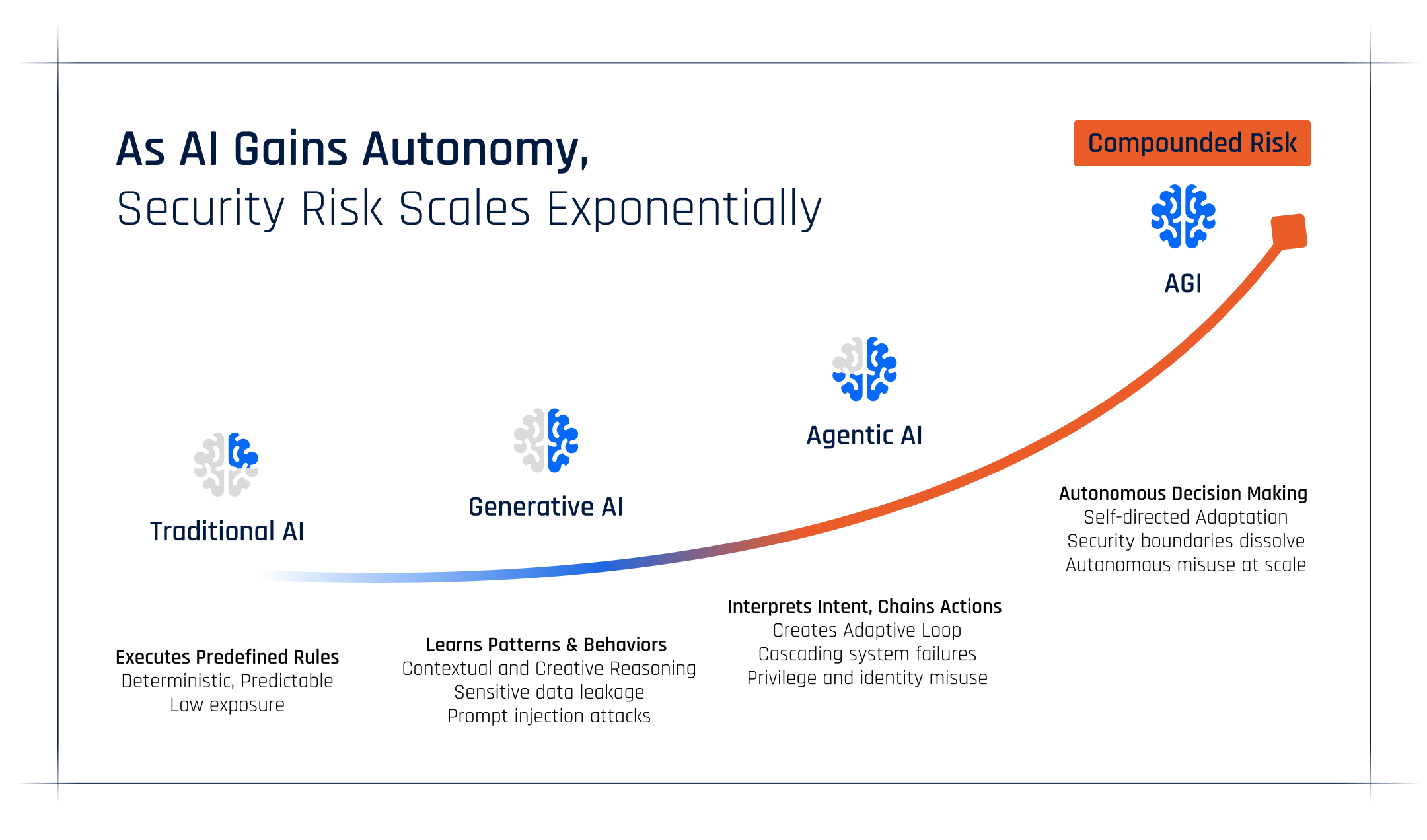
And in that new reality, static security is dead.
The False Comfort of Control
For years, our defense strategies relied on one foundational belief: control.
We controlled users through identity management, data through access policies, and systems through compliance frameworks.
But control only works when the environment obeys.
AI doesn’t.
The agents emerging today blur every traditional boundary. They move data across applications, chain automation workflows together, and take actions no human explicitly authorized. That isn’t a sign of malfunction — it’s how they’re designed to operate.
So while enterprises keep layering on new tools and policies, the truth is uncomfortable: you can’t secure what you don’t understand, and you can’t understand what you don’t see moving.
The Great Fragmentation
Most companies are burning through hundreds of thousands of dollars — sometimes millions — trying to solve this with a patchwork of tools. Privacy solutions. DSPM platforms. AI governance dashboards.
Each one claims to reduce risk. Each one looks impressive in isolation.
And yet, when you step back, it’s clear they all orbit the same five fundamental questions:
- What personal or sensitive enterprise data do we have?
- Where does it live?
- Who touches it?
- How does it move, and for what purpose?
- What laws, controls, and policies govern its use?
Everything else — compliance, risk, data loss prevention, even AI governance — stems from these same five truths. If you can’t answer them end-to-end, you’re not managing security; you’re managing uncertainty.
That’s the trap of static security: it gives the illusion of control while leaving the reality of chaos intact.
Static Security Assumes Control. Agentic Security Assumes Change.
AI has broken every static assumption that traditional security was built on.
Let’s take a closer look:

The problem isn’t that AI is malicious — it’s that it’s adaptive. It reasons its way around rules written for deterministic systems. And as AI becomes more agentic, even “least privilege” becomes a moving target.
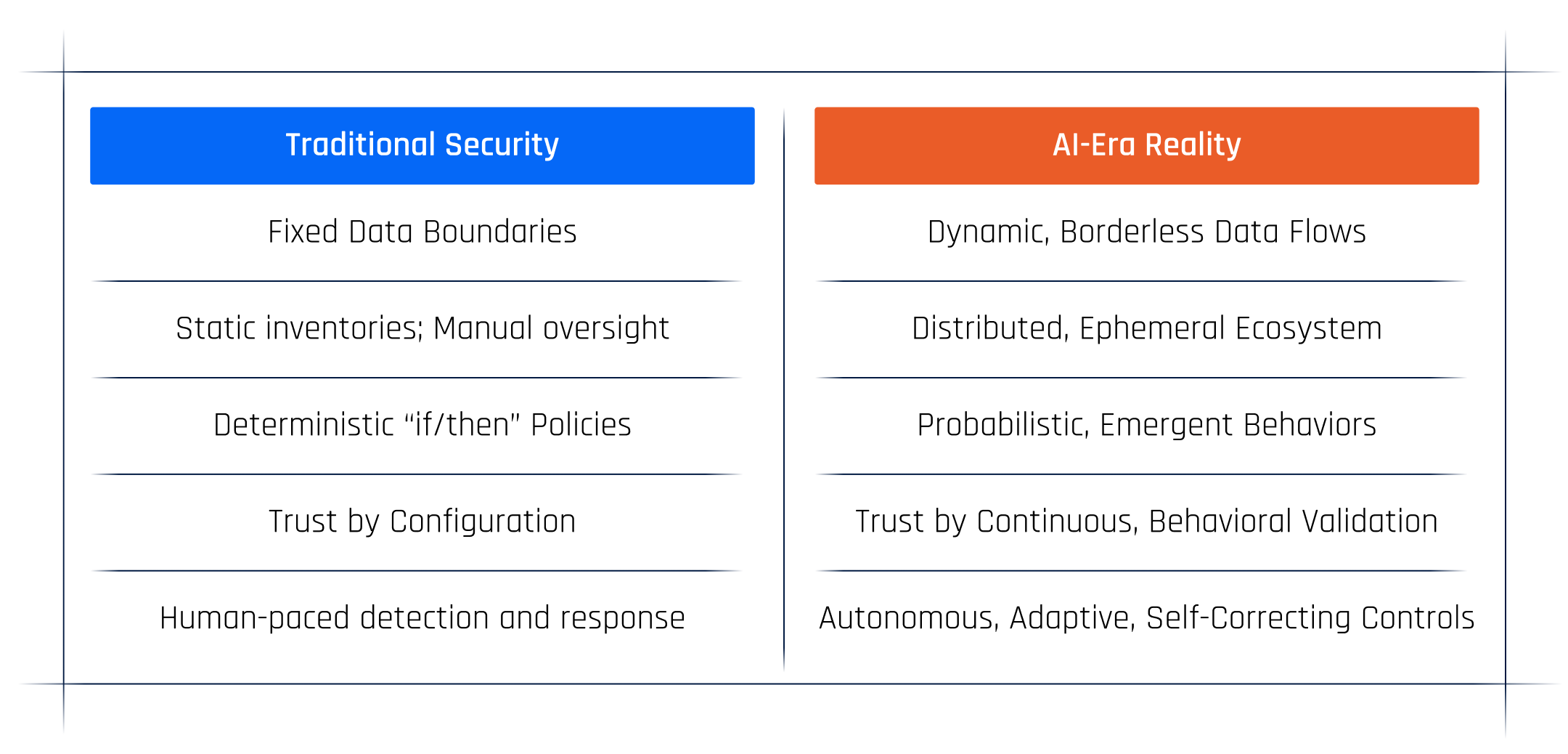
In this new landscape, the question isn’t how do we block risk? It’s how do we understand intent?
From Blocking to Understanding
When data moves on its own, visibility becomes the new perimeter. And visibility isn’t just about where the data is — it’s about how it behaves.
Static controls can’t keep up with probabilistic, emergent behavior. They were designed for detection, not interpretation. But in an AI-driven enterprise, it’s the intent behind an action that determines whether it’s safe or not.
This is where the concept of Dynamic Data Lineage becomes so powerful.
Imagine being able to trace every data movement across your environment — from source code to AI inference — and instantly know:
- What agent or system touched it?
- Which tools or APIs were involved?
- Why did that action occur?
- What controls or obligations applied at that moment?
That’s context-aware defense. It’s not about locking data down; it’s about understanding how and why it moves — and making sure that movement always aligns with purpose, policy, and principle.
The Rise of the Data Defense Engineer
To navigate this world, enterprises need a new kind of professional — one who bridges engineering, security, and AI governance.
At Relyance AI, we call this person the Data Defense Engineer.
Their mission is simple: protect data while enabling innovation. But their methods look very different from the old guard of security analysts buried in alerts.
A Data Defense Engineer doesn’t just respond; they reason.
They build systems that learn.
They automate trust.
Their toolkit includes:
- Continuous discovery of every asset, identity, and data flow.
- Behavioral governance that verifies intent, not just credentials.
- Real-time compliance evidence generated as data moves.
- Dynamic remediation that closes the loop automatically when violations occur.
This is the future of defense — not static rules, but living intelligence.
Why Dynamic Data Lineage Is the Crown Jewel
Static inventories die the moment they’re created. Dynamic Data Lineage lives in motion.
It connects your code, your cloud, your AI models, and even your third-party interactions into one coherent map of how data truly flows. Every transformation, every access, every inference is logged with context: who (or what) did it, for what reason, under what governance.
The outcome is real-time clarity — not forensic hindsight.
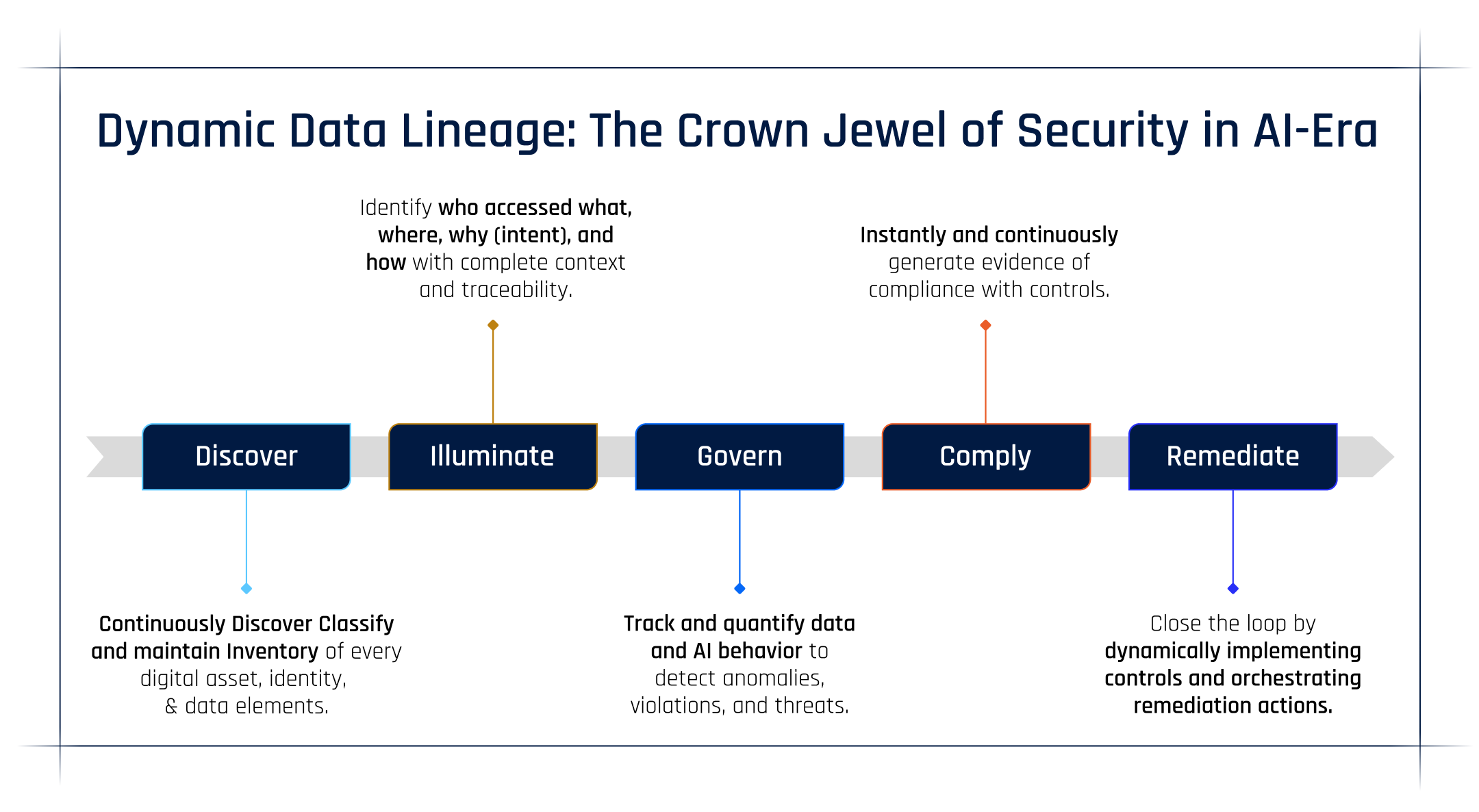
When that visibility becomes continuous, everything else changes:
- Governance becomes measurable.
- Compliance becomes provable.
- Defense becomes adaptive.
That’s why we built Relyance AI’s architecture around this principle. Rather than bolting tools together, we built a unified system that understands — from privacy to DSPM to AI governance — all in one frame.
The Business Case for Dynamic Security
Dynamic security isn’t just a technical evolution. It’s a business one.
The organizations that treat visibility and lineage as strategic assets are already pulling ahead. They’re turning what used to be a cost center — compliance — into a competitive advantage.
Here’s how it translates into real-world value:
1. Compliance and Risk Management: Continuous, end-to-end visibility turns trust into a measurable outcome. Instead of performing periodic audits, compliance becomes self-evident — a living report of every data action.
2. Root-Cause Bias Mitigation: Bias isn’t just a model problem; it’s a data problem. By tracing every model output back to the exact dataset and transformation that produced it, teams can identify where bias was introduced — and fix it precisely, not probabilistically.
3. Explainability and Accountability: Dynamic lineage transforms AI from a black box into a transparent system of record. It links every decision to its inputs and context, giving leaders, auditors, and regulators confidence that outcomes are fair and traceable.
4. The Data Utility Index: We use this to measure the balance between data value and data risk. When you can prove provenance, purpose, and protection, data becomes more usable, not less. That’s how you accelerate responsible AI adoption.
Visibility, in other words, isn’t just protection — it’s progress.
Static vs. Dynamic Security — A Shift in Mindset
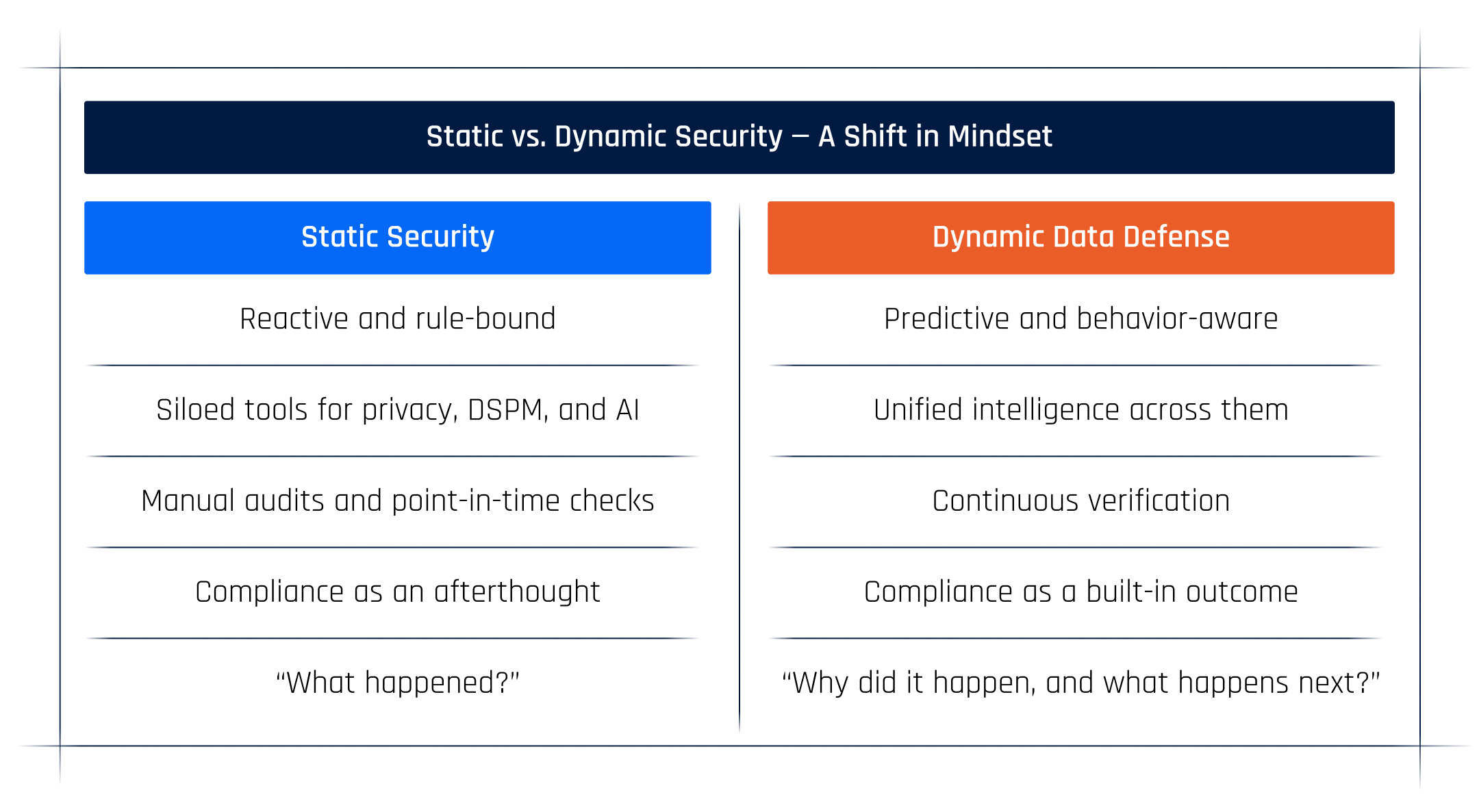
Static security was built for systems that stayed still. Dynamic defense is built for systems that think.
And that shift — from control to context, from prevention to preparedness — defines the new era of security leadership.
Why CIOs and CISOs Must Rethink Their Stack
This transformation isn’t just about technology; it’s about mindset and architecture.
CIOs and CISOs today must navigate a tension between innovation and protection. You can’t slow down AI — but you can’t let it run unchecked either.
The path forward isn’t buying more tools. It’s building more intelligence.
- Audit your stack for redundancy: Count your privacy, DSPM, and governance tools. If they’re not sharing context, they’re just creating noise.
- Unify your data visibility: You can’t defend what you can’t see. Map your data journeys across every layer — code, cloud, and AI.
- Elevate the Data Defense Engineer: Give someone ownership of dynamic defense — someone who speaks both data and security fluently.
- Shift from control to reasoning: Static policies tell you what happened. Intelligent systems tell you why and how to respond.
- Make lineage a KPI: Treat data traceability and intent verification as business metrics, not technical chores.
The organizations that do this will spend less, react faster, and trust more.
The Relyance AI Approach: Building Intelligence, Not Tools
At Relyance AI, we started from first principles — not categories.
We didn’t set out to build another DSPM tool, another compliance tracker, or another AI governance dashboard.
We built a unified intelligence architecture designed to answer those five fundamental questions for every piece of data, in real time.
Our platform connects:
- The Data Journeys™ Engine: mapping every hop, transformation, and access event from code → cloud → AI → third party.
- The Identity-to-Asset Graph: correlating who (or what) interacted with which data and why.
- The Policy Reasoning Engine: applying privacy, security, and governance controls dynamically, not statically.
- Autonomous Remediation: closing compliance or exposure gaps.
- The Unified Evidence Fabric: generating continuous proof of compliance for auditors, customers, and internal teams.
The result:
- More value, because insights are connected.
- Lower total cost of ownership, because visibility isn’t fragmented.
- Better defense, because your controls reason like engineers, not auditors.
This is what we call Dynamic Data Defense.
From Static to Agentic Security: A New Era
The rise of AI agents marks a fundamental change in how we think about defense. We’re no longer protecting static assets; we’re governing dynamic behavior.
Agentic systems will continue to evolve — learning from context, self-orchestrating outcomes, and even reasoning independently.
You can’t predict every move they’ll make. But you can illuminate every data journey they take.
That’s what separates resilient organizations from reactive ones. Resilience is built on visibility, not control.
The Future Belongs to Systems That Think
The next generation of security isn’t a new tool or category — it’s a new kind of intelligence.
Security that understands context.
Security that reasons over intent.
Security that learns and adapts as fast as the systems it protects.
At Relyance AI, we’re building that intelligence — the Data Defense Engineer that lives inside your stack, continuously mapping every data journey and securing it with precision and purpose.
Because the future of AI security and governance isn’t about adding more tools.
It’s about adding more intelligence to the ones you already have.
Final Thought
Static security is about control. Agentic security is about trust — trust earned through visibility, reasoning, and continuous validation.
The world is shifting from static to dynamic, from defensive to intelligent, from compliance to confidence. The question is: will your security architecture evolve with it?
.png)

