Most comprehensive
data security intelligence
Powered by our Data Graph, transform fragmented data security approaches into a unified data security platform that illuminates your data's entire journey. Stop chasing shadows. Discover, classify, and secure your sensitive data across all environments.


Tired of piecemeal solutions?
Our Unified Security Posture Management capability addresses most pressing obstacles when securing data across complex, multi-dimensional ecosystems while dealing with data sprawl and overprovisioning.
Fragmented data visibility
Lack of a unified view of all AI systems, making it difficult to identify risks and ensure consistent governance across your organization.You struggle to identify and understand where your sensitive data resides across diverse cloud environments, SaaS applications, and on-premises systems, leading to blind spots and potential security risks. The Archipelago of unseen data is unacceptable.
Policy chaos across disparate data realms
Maintaining consistent data security policies across disparate systems and teams is a significant challenge, increasing the risk of policy drift, compliance violations, and unauthorized data access while AI-driven transformations introduce novel threats.
Manual or inefficient data security
Relying on manual or regex-based processes for data discovery, classification, and security configuration is time-consuming, error-prone, full of false positives, and unable to keep pace with the ever-increasing volume and complexity of data. You need to break free from this operational black hole.

Multi-source contextual classification
Combine direct database connections, source code analysis, and real-time observability data to build a comprehensive, context-rich view of your assets from origination through transformation to data storage that traditional DSPM solutions cannot match.
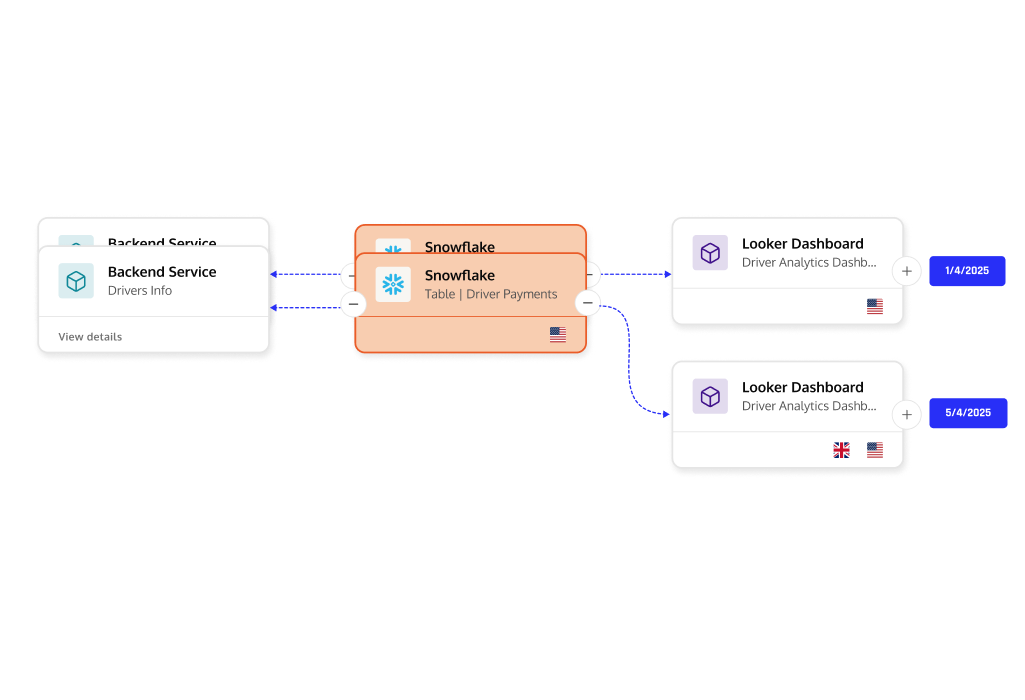
Advanced schema management with temporal intelligence
A significant enhancement is our approach to schema management. The platform:
- Captures multiple schemas per table
- Tracks schema evolution over time
- Provides column-level visibility within tables

Identity-centric security monitoring
Track which human and machine identities have access to specific data assets across both cloud resources and third-party SaaS applications, identifying excessive permissions and risky access patterns.

X-Ray vision for your asset intelligence
Understand data lineage, access patterns, and risk concentrations in a way that empowers proactive decision-making and strengthens your overall security strategy.
The intelligence engine for Trust & Governance
Unlock complete data visibility and continuous compliance with our proprietary platform that illuminates your entire digital ecosystem.




Relyance AI difference
Unified privacy and DSPM
Stop juggling disparate tools and vendors. Relyance AI is the only platform that converges global privacy compliance and DSPM, providing a single pane of glass to manage risk across your entire digital landscape – a true force multiplier for your security team.
Intelligent automation
Our AI-driven automation built on TrustiQ isn't just about efficiency; it's about resilience. It works tirelessly in the background, proactively identifying and mitigating threats, freeing up your team to focus on strategic initiatives, and ensuring your data remains secure 24/7.
Prove trust, not just claim it
In today's world, trust is paramount. Relyance AI provides clear visibility, proactive controls, and auditable compliance records. You need not just claim you're secure but also prove it to your stakeholders, customers, and regulators, building unwavering confidence.


