Data in Motion:
DSPM and cloud security posture
Secure every sensitive data flow, achieve audit-ready compliance, and build a dynamic security posture for the cloud era.
Featured

DSPM: The definitive guide to cloud security & compliance
Dynamic DSPM vs. Static DSPM: The architecture difference

DSPM vendors for the AI era: Prioritizing data flows over static inventories
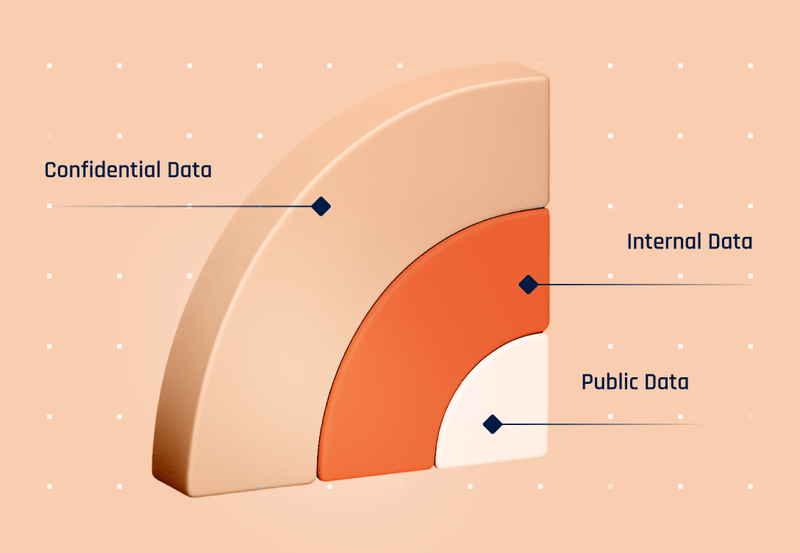
What is data classification in information security? (Plain-English guide)
Explore related resources
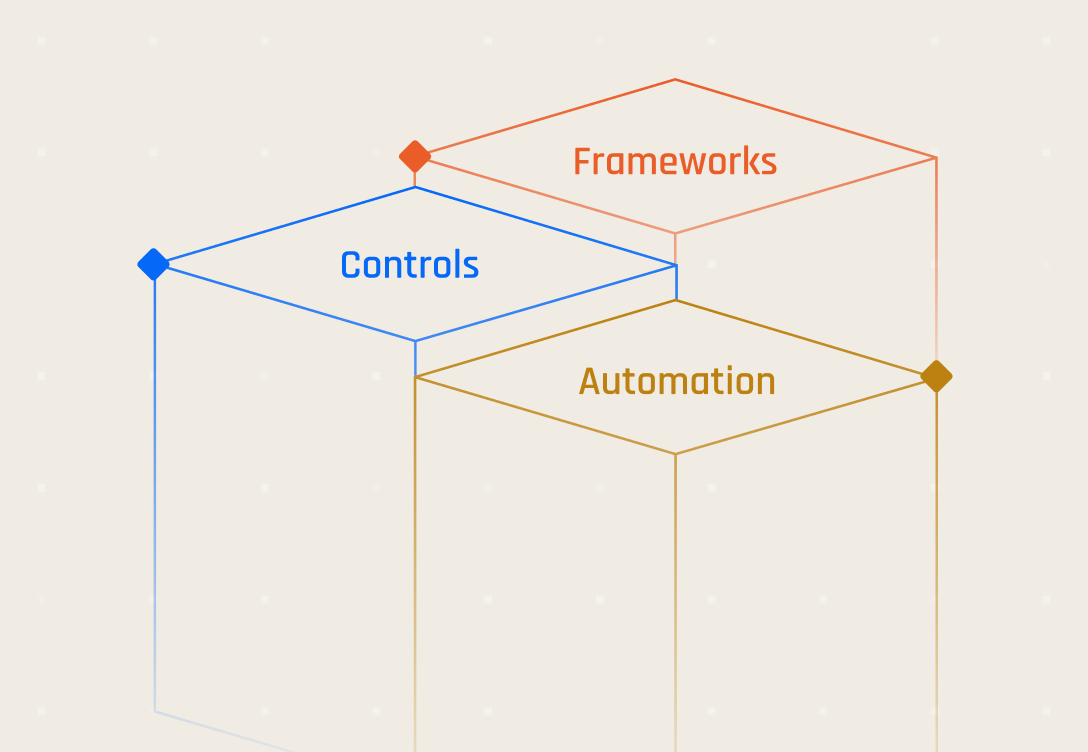
Data-Security Compliance—Frameworks, controls & automation for 2025
Data Classification in Cybersecurity: Methods and Levels
How to run a data-security risk assessment in AI systems (A step-by-step template)
Contributors
Track Your Complete AI Footprint Now
Data Security FAQ
What is Data Security Posture Management (DSPM) and how does it differ from traditional security tools?
DSPM continuously discovers sensitive data, classifies it with business and regulatory context, observes how it flows between systems, maps access permissions, and enforces policy through automated controls. Unlike traditional tools, DSPM centers on the data itself rather than infrastructure. CSPM hardens cloud configurations, DLP blocks exfiltration events, and CIEM manages identity permissions—but DSPM complements these by tracking data content, context, flows, and compliance obligations across the entire stack. Modern DSPM illuminates runtime data movement between SaaS apps, APIs, and AI models where real-world risks live, providing a unified real-time view rather than disjointed snapshots of data at rest.
Why is context-rich data classification critical for effective DSPM?
Traditional taxonomies like "Public/Internal/Confidential" are too crude for today's regulatory reality. Modern classification uses descriptive, context-aware labels mapping directly to regulations and business meaning—like "Special-Category Personal Data" signaling GDPR Article 9 obligations requiring stronger encryption and residency constraints. Effective classification enriches labels with vendor origin, data subject type, and processing purpose, transforming classification from a label into a policy switch. Breach post-mortems repeatedly show that missing or vague labels prevented proper controls from firing—allowing over-privileged accounts, stale backups, or unsanctioned copies to become full-blown incidents. Accurate classification is the difference between contained alerts and headlines.
What capabilities should organizations prioritize when implementing DSPM?
Organizations should focus on six critical capabilities:
- First, continuous discovery and classification across cloud accounts, data warehouses, SaaS, and AI repos as data is created.
- Second, lineage and data-flow mapping revealing how sensitive fields traverse ETL processes, APIs, backups, and models—critical for incident impact analysis and demonstrating purpose limitation compliance.
- Third, identity overlay correlating users, roles, and service accounts with datasets to expose over-privilege.
- Fourth, policy-as-code with continuous controls monitoring including Gen-AI guardrails that redact regulated data before reaching models.
- Fifth, automated remediation enabling quarantine, encryption, access revocation, and ticket creation.
- Sixth, compliance automation maintains always-fresh audit trails tied to frameworks like ISO 27001, SOC 2, and GDPR.