The old security playbook is broken. For years, we were taught to build a fortress around our data, with high walls and a single gate. But the reality of 2025 is that the fortress has dissolved. Your data, your most valuable asset, is no longer neatly tucked away on a server down the hall. It’s flowing through a sprawling digital landscape of cloud services, SaaS applications, AI pipelines, and third-party vendor tools.
This new reality has left many security leaders with a constant, nagging anxiety, trying to answer a simple but terrifying question: Where is our sensitive data, who can touch it, and is it truly safe?
This is where Data Security Posture Management (DSPM) comes in, not as just another tool, but as a fundamental shift in how we see and protect data. It’s a strategy designed for the world as it is complex, decentralized, and in constant motion. It’s about moving beyond reactive defense and building a dynamic, intelligent security posture that turns trust into your greatest competitive advantage.
Things you’ll learn
- What DSPM is and how it differs from CSPM/DLP/CIEM.
- How to map data flows, identities, and classification to strengthen..
- A practical rollout plan using policy-as-code, automation, and Gen-AI guardrails.
- How to evaluate data security posture management vendors and quantify ROI.
Why DSPM and why now
Cloud and SaaS dissolved the old perimeter. Sensitive data now moves across buckets, databases, APIs, developer sandboxes, partner tools, and AI pipelines. Regulations multiply each year, and boards increasingly demand audit-ready proof, not slideware.
Contracts routinely require SOC 2 or ISO 27001, and fines for mishandling special-category data keep rising. In this climate, posture at the data layer is non-negotiable: you must know what data you have, how it moves, who can touch it, and whether each use aligns with data security compliance obligations.
What is Data Security Posture Management?
DSPM continuously discovers sensitive data, classifies it with business and regulatory context, observes how it flows between systems, maps who and what can access it, and enforces policy through ongoing controls and automated remediation. Unlike tools that only scan “data at rest,” modern DSPM shines a light on runtime data movement that flows between SaaS apps, APIs, and AI models where many real-world risks live.
A mature program couples discovery and classification with identity-to-data mapping, lineage, and policy-as-code, producing an authoritative, single, real-time view of data risk rather than disjointed snapshots. That unified view is also what powers faster, more accurate data security risk assessment across business units.
DSPM vs. adjacent tools (quickly)
- CSPM hardens cloud service configurations.
- DLP attempts to block exfiltration events.
- CIEM manages identity permissions at scale.
DSPM complements these by centering on the data itself content, context, flows, and obligations and then orchestrating controls across the stack to keep you continuously aligned with compliance requirements.
What “good” classification looks like (and why labels matter)
Traditional “Public / Internal / Confidential” taxonomies are too crude for today’s risk and regulatory reality. Teams now use descriptive, context-aware labels that map directly to regulations and business meaning e.g., a “Special-Category Personal Data” label signals GDPR Article 9 obligations, stronger encryption, and residency constraints.
The upgrade is context enrichment: along with the sensitivity, capture vendor of origin (e.g., Stripe vs. Salesforce), data subject (customer/employee/partner), and processing purpose (billing, analytics, R&D). This turns classification from a label into a policy switch. In practice, high-precision programs blend three lenses: content inspection (patterns/NLP/ML), context inference (paths, apps, tags), and human judgment (owner overrides).
If you’re building or modernizing your taxonomy, anchor it to data classification in cyber security, data classification security, and the educational angle of data classification in information security so non-experts understand why labels drive controls.
When classification fails: lessons from breaches
Breach post-mortems repeatedly show that missing or vague labels were silent accomplices. The absence of the right label meant the right controls didn’t fire so over-privileged accounts, stale backups, or unsanctioned analytics copies became full-blown incidents. Accurate classification is the difference between a contained alert and a headline.
Common failure patterns include mis-labeled analytics exports, untagged staging copies, and backups without “high-impact” flags, so sensitive fields slip into broad access groups. This also derails compliance workflows: without proper labels and lineage, breach notifications, DPIAs, and contractual reporting timelines stall or miss scope.
Prevent this by enforcing context-rich labels at data creation (rooted in data classification in cyber security), auto-validating with scheduled scans/canary datasets, and wiring labels to IAM/DLP policies so controls trigger automatically.
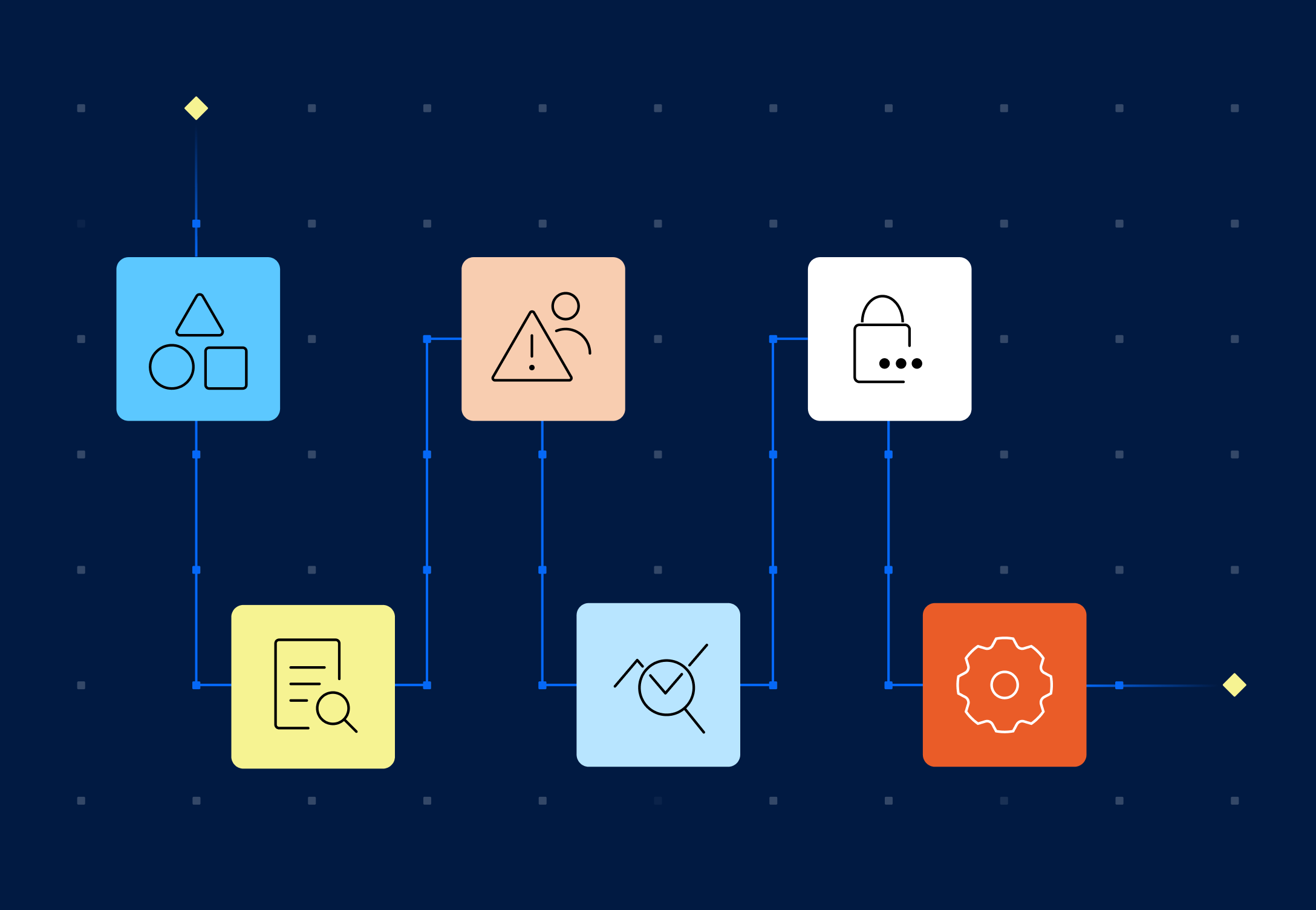
How modern DSPM actually works
- Continuous discovery & classification across cloud accounts, data warehouses, SaaS, code and AI repos as data is created, not months later.
- Lineage & data-flow mapping to reveal how sensitive fields traverse ETL, APIs, backups, and models. This is critical for incident impact analysis and to demonstrate purpose limitation under compliance.
- Identity overlay that correlates users, roles, service accounts, and third parties with specific datasets to expose over-privilege and risky access paths.
- Policy-as-code & continuous controls monitoring, including Gen-AI guardrails that redact or block regulated data before it’s sent to models.
- Automated remediation, quarantine, encryption, access revocation, and ticket creation, so posture isn’t just observed, it’s improved.
The outcome is a living, unified view of data risk that security, privacy, and governance teams can share with confidence and a better foundation for rolling data security risk assessment into routine operations.
The compliance backbone behind DSPM
Organizations rarely operate against a single rulebook. Most combine ISO 27001 and NIST CSF with sectoral and regional obligations like SOC 2, CMMC 2.0, and DORA. A resilient DSPM program maps controls to these frameworks and keeps evidence continuously current, not just during audit season.
Foundational controls, encryption and strong key management, Zero-Trust IAM, contextual DLP based on accurate classification, continuous monitoring and logging are the “always on” layer that DSPM instruments and proves. All of this is table-stakes for passing audits and substantiating compliance claims.
Best practices for data security posture management
- Start with crown-jewel clarity: Inventory customer PII/PHI, financials, regulated logs, source code, and model training data, then apply context-rich labels that encode vendor, subject, and purpose. This is what turns classification into enforcement and audit proof.
- Watch the flows, not just the files: Inventory at rest leaves you blind to risky runtime movement. Platforms that unify flow lineage, identity relationships, and regulatory context give teams a shared, defensible picture of risk and accelerate data security risk assessment.
- Close the loop with automation: Finding problems is table stakes; auto-remediation (encrypt, quarantine, revoke access, open tickets) and Gen-AI guardrails make posture real.
- Measure what matters: Replace vulnerability laundry lists with an executive view that rolls data risk into a single score per business unit. That’s the language boards and regulators expect in compliance reviews.
- Continuously test and iterate: Treat risk assessment as an always-on, data-driven process, not a once-a-year fire drill. Bake simulations and canary datasets into pipelines to validate controls.
A practical rollout plan (six stages)
Stage 0: Define scope & obligations. Identify your frameworks (e.g., ISO 27001, NIST CSF, SOC 2, CMMC 2.0, DORA), risk appetite, and data owners. Align early with legal/privacy so data security compliance requirements translate into concrete controls.
Stage 1: Connect & discover. Integrate major clouds, data stores, and SaaS. Use content+context+owner input to achieve high-precision classification without drowning in false positives. Document assumptions for later data security risk assessment cycles.
Stage 2: Map identities and flows. Build lineage across ETL, APIs, and AI pipelines; overlay identities and service accounts to uncover misuse and over-privilege.
Stage 3: Encode policy as code. Translate encryption, residency, retention, and AI policies into rules that can be continuously monitored and enforced; prioritize by blast radius using graph context.
Stage 4: Automate remediation. Quarantine, encrypt, and revoke access automatically; open tickets with adequate context so engineers resolve fast.
Stage 5: Operationalize compliance. Shift to continuous: automate ROPAs, DSARs, and evidence collection; keep an always-fresh audit trail tied to data security compliance.
Stage 6: Review & iterate. Posture is dynamic; monitor controls continually, and re-assess after architectural or regulatory changes. Fold results back into the data security risk assessment program.
Buyer’s checkpoint: capabilities that matter in 2025
When shortlisting DSPM platforms, insist on live demos showing end-to-end flow mapping (including 24-hour playback), risk scoring that fuses identities and business context, Gen-AI guardrails, native connectors across major stores, frank accuracy metrics at scale, and seconds-level auto-remediation. Ask how the platform respects data residency and feeds findings bi-directionally into IAM, EDR, SIEM/SOAR, and GRC.
This is where you separate marketing claims from operational outcomes and it’s also where you’ll evaluate the broader market of DSPM vendors and even top-rated security companies for data compliance that complement your stack.
Real-world impacts you should expect
- Over-privilege eliminated: Identity overlays reveal third-party or contractor accounts reading special-category data they don’t need; access is revoked and blast radius shrinks.
- Spreadsheet toil reduced: Privacy teams automate classification across thousands of stores, cutting manual effort dramatically and freeing engineers for higher-value work.
- Board-level clarity: Instead of vulnerability inventories, CISOs show a single risk score by business unit, tying posture to revenue and strategy, exactly what compliance stakeholders want to see.
How Relyance AI operationalizes DSPM
Relyance AI is built for this modern vision: AI-native discovery and classification that runs continuously as new data appears; labels enriched with business and regulatory context; and Data Journeys™, a graph-powered lineage view of how information flows through apps, APIs, and AI pipelines. Teams use these capabilities to surface hidden transfers, automate DPIAs and ROPAs, and maintain auditable proof without spreadsheet sprawl.
Crucially, Relyance ties intelligence to action: policy-as-code with continuous monitoring, automated remediation (quarantine, encrypt, revoke access, open tickets), and Gen-AI guardrails that redact or block regulated data before it reaches a model, while logging each attempted leak for audit.
The result is a living, unified risk view that security, privacy, and governance can trust and act on, plus a stronger foundation for recurring data security risk assessment and clear-headed vendor comparisons across DSPM vendors.
Final notes
DSPM has become the operating system for data-centric security: understand what you have, see how it moves, know who can touch it, enforce policy in real time, and prove compliance on demand. The organizations that win won’t merely inventory data at rest; they will master data-in-motion, automate evidence, and close the loop with remediation.
With the right program and platform, DSPM shifts from a defensive expense to a trust amplifier and a practical engine for faster, safer innovation.