What if the biggest threat to your data isn't a hacker, but a blind spot you never knew existed?
Today this question isn't just rhetoric—it's a critical business reality. Data floods every corner of our organizations, powering innovation, driving decisions, and, yes, attracting a relentless barrage of threats. Ignoring the potential for a data breach isn't just naive; it's a gamble with your reputation, customer trust, and bottom line.
So, how do you get a firm grip on your data's vulnerabilities before they become front-page news? The answer lies in a robust data security risk assessment.
Forget dusty checklists and once-a-year fire drills. A true assessment is a living, breathing process that helps you understand where your critical data lives, who has access, what could go wrong, and how badly it would hurt. It’s about being proactive, not just reactive. To establish this proactive, living defense system across all your data, visit our definitive guide on Data Security Posture Management (DSPM).
What exactly is a data security risk assessment?
At its heart, a data security risk assessment is a systematic process to identify, analyze, and evaluate the potential risks to your organization's information assets. It’s about understanding the likelihood of a threat exploiting a vulnerability and the potential impact if it does.
Think of it as a health check-up for your data security posture – uncovering hidden weaknesses before they become critical illnesses. This isn't just about compliance (though it’s crucial for that too). It’s about making informed decisions, prioritizing resources, and building a more resilient organization.
Your step-by-step template to a meaningful assessment
Ready to roll up your sleeves? Here’s a practical framework to guide you:
Step 1: identify and inventory your data assets
- The core idea: You can't protect what you don't know exists. This initial phase is all about discovery.
- Action: Map out all the places sensitive data resides: databases, cloud storage, endpoints, applications, AI models, even third-party systems. What kind of data is it? (e.g., PII, PHI, financial records, intellectual property, AI training data). Who owns it?
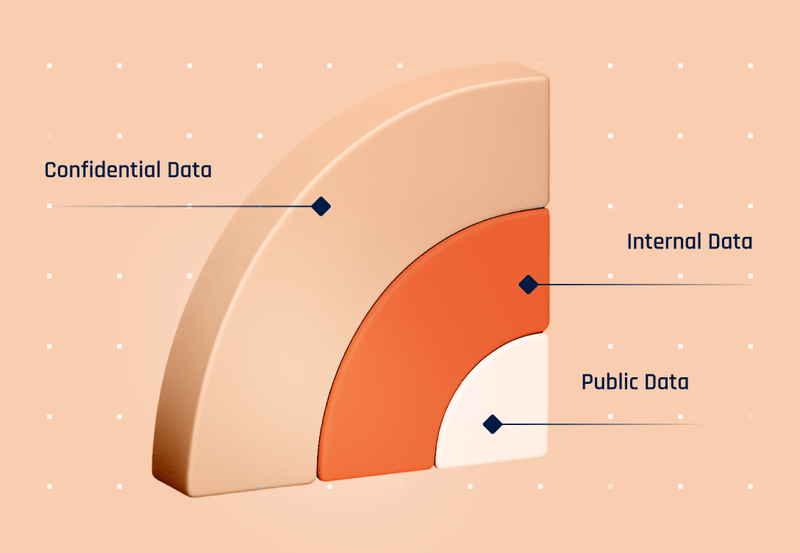
Step 2: classify your data
- The core idea: Not all data is created equal. Some data, if compromised, would be a minor inconvenience; other data could be catastrophic.
- Action: Categorize your inventoried data based on its sensitivity and criticality. Consider legal requirements (like GDPR, CCPA, HIPAA), business impact, and contractual obligations. This helps prioritize your protection efforts.
Step 3: identify threats and vulnerabilities
- The core idea: Think like an attacker (and also like an employee who might make an honest mistake).
- Action: Brainstorm potential threats: malicious insiders, external hackers, malware, ransomware, phishing, accidental deletion, system failures, natural disasters, even vulnerabilities in your AI development lifecycle. Then, identify vulnerabilities: unpatched software, weak passwords, misconfigured cloud services, lack of encryption, inadequate access controls, or insecure data flows.
Step 4: analyze risks and potential impact
- The core idea: This is where you connect the dots between threats, vulnerabilities, and your assets.
- Action: For each identified threat/vulnerability pair targeting a data asset, assess the likelihood of it occurring and the potential impact (financial, reputational, legal, operational). A simple high/medium/low scale can work, or you can use more quantitative measures. This helps you prioritize which risks need immediate attention.
Step 5: develop and implement controls
- The core idea: Now that you know the risks, what are you going to do about them?
- Action: Based on your risk analysis, decide on appropriate controls. These can be technical (firewalls, encryption, MFA), administrative (policies, training, incident response plans), or physical (locked server rooms). Prioritize controls that address high-impact, high-likelihood risks. Document these controls and assign responsibility for implementation.
Step 6: monitor, review, and iterate
- The core idea: The threat landscape, your systems, and your data are constantly changing. Your risk assessment can't be a static document.
- Action: Continuously monitor your controls to ensure they're working effectively. Regularly review and update your risk assessment – annually at a minimum, or whenever significant changes occur (new systems, new regulations, emerging threats). Learn from any incidents or near-misses.
The future of risk assessment
Running these assessments traditionally involves a mountain of spreadsheets, endless interviews, and a snapshot-in-time view that’s often outdated before it’s even finalized. What if you could automate the discovery, inventory, and classification? Imagine your risk posture continuously updated, not just when an auditor comes knocking. This isn't a far-off dream; it's where the industry, and smart data governance, is heading.
This is precisely where Relyance AI steps in, transforming the data security risk assessment from a periodic, manual chore into a continuous, automated, and intelligent process. Relyance AI automates the discovery, inventory, and classification of data, systems, and even AI models, assessing regulatory, operational, and ethical risks to auto-generate executive AI-risk summaries.
This extends to your supply chain with automated third-party vendor assessments that map data flows to contracts, raising real-time flags. The platform ensures you’re always audit-ready, maintaining tamper-proof evidence and eliminating the scramble for manual prep. It’s about moving from static snapshots to an always-on, dynamic understanding of your risk.
Taking control of your data destiny
A thorough data security risk assessment is no longer a "nice-to-have." It's fundamental to protecting your organization in an increasingly complex digital world.
By systematically understanding your assets, threats, and vulnerabilities, you can make smarter security investments, build resilience, and ultimately, turn your data from a potential liability into your most powerful, well-protected asset.
The journey might seem daunting, but taking that first step is crucial. Because in the world of data, what you don't know can hurt you—profoundly.