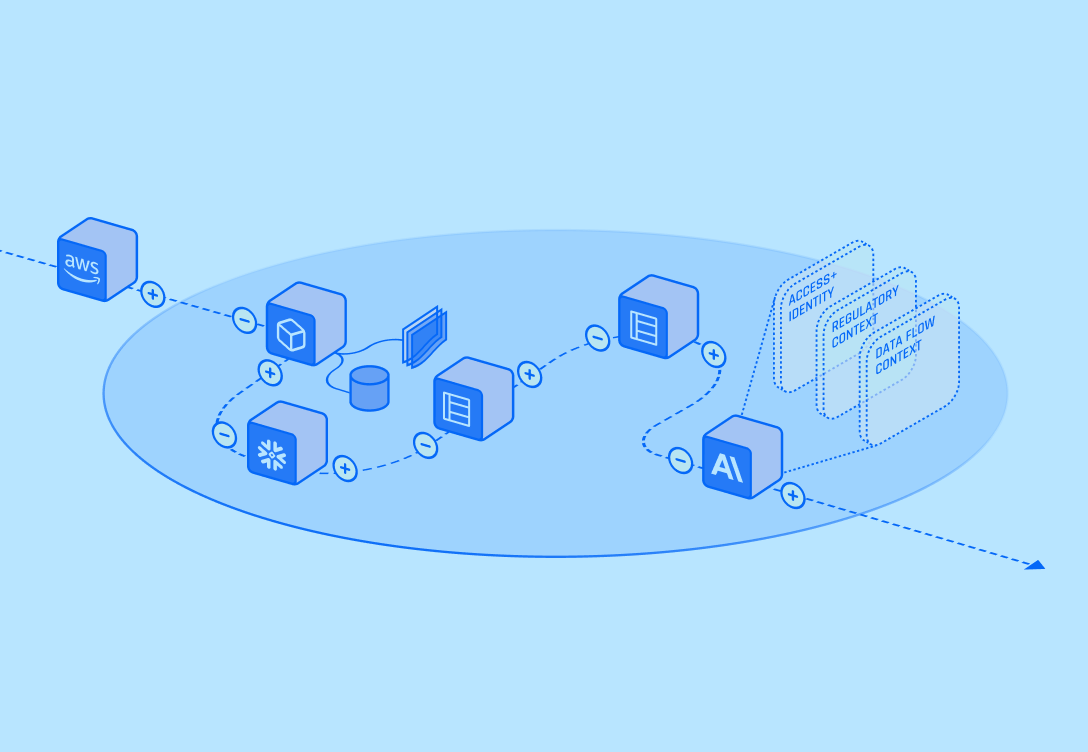
The Multi-Cloud Reality
Organizations increasingly operate across multiple cloud platforms, with most enterprises using an average of 3.4 cloud providers simultaneously. This multi-cloud approach provides operational resilience, vendor diversification, and access to best-of-breed services, but creates unprecedented data security complexity that traditional DSPM tools cannot handle effectively.
Multi-cloud environments generate data flows that span AWS, Microsoft Azure, Google Cloud Platform, and numerous SaaS applications. Data moves between cloud providers through APIs, cross-cloud networking, and hybrid integration platforms, creating visibility challenges that siloed security tools cannot address comprehensively.
The Siloed Security Problem
Platform-Specific Tool Limitations
AWS Security Tools: Provide deep visibility into AWS services but cannot track data flows to Azure or Google Cloud Azure Security Center: Monitors Microsoft ecosystem effectively but loses visibility when data moves to other cloud platforms
Google Cloud Security Command Center: Offers comprehensive GCP monitoring but cannot follow data to external cloud providers SaaS Security: Individual applications provide security logging but cannot track data flows to other platforms
Visibility Gap: Organizations using platform-specific tools see fragments of their data security posture rather than comprehensive multi-cloud visibility.
Cross-Cloud Data Flow Blindness
API Integration Challenges: Data moving through cross-cloud APIs remains invisible to platform-specific monitoring tools
Hybrid Connectivity: VPN connections, direct network links, and hybrid integration platforms create data pathways that individual cloud security tools cannot monitor
SaaS-to-Cloud Flows: Data moving from SaaS applications to cloud infrastructure or between different SaaS platforms escapes single-platform monitoring
Edge Computing: Data processing at edge locations across multiple cloud providers creates additional visibility gaps
Security Impact: Organizations cannot assess data security risks when they cannot see complete data flows across their multi-cloud environment.
Operational Complexity
Multiple Security Dashboards: Security teams must monitor separate interfaces for each cloud platform and major SaaS application Inconsistent
Alert Formats: Different platforms generate alerts with varying formats, severity levels, and investigation procedures
Correlation Challenges: Manual correlation of security events across platforms consumes significant analyst time and often misses multi-platform attack patterns
Policy Inconsistency: Difficulty maintaining consistent security policies across platforms with different capabilities and interfaces
Operational Impact: Security teams cannot operate efficiently when managing multiple siloed security tools with different interfaces and capabilities.
Multi-Cloud Data Patterns
Cross-Cloud Data Processing Workflows
Modern applications routinely process data across multiple cloud platforms:
Example: E-commerce Platform
- Customer data stored in AWS RDS
- Product recommendations generated using Google Cloud AI
- Payment processing through Azure-hosted services
- Analytics processed in Snowflake on multiple cloud platforms
- Customer communications managed through Salesforce
Traditional DSPM Challenge: Individual platform tools cannot track this complete data flow, leaving significant security and compliance blind spots.
Hybrid AI Workloads
AI applications frequently use services from multiple cloud providers to optimize performance and capabilities:
Example: Financial Services AI
- Training data stored in AWS S3
- Model training performed on Google Cloud AI Platform
- Model serving through Azure Machine Learning
- Real-time inference data flowing through AWS Lambda
- Results stored in multi-cloud data warehouses
Visibility Problem: Platform-specific AI monitoring tools cannot provide comprehensive visibility into multi-cloud AI workflows.
Multi-Cloud Disaster Recovery
Organizations implement disaster recovery strategies that span multiple cloud providers:
Example: Healthcare System
- Primary patient data in Azure
- Real-time backup replication to AWS
- Disaster recovery testing on Google Cloud
- Archive storage distributed across multiple providers
- Emergency access through various SaaS platforms
Compliance Challenge: Regulatory requirements demand complete audit trails that single-platform tools cannot provide for multi-cloud disaster recovery workflows.
The Integration Challenge
API Compatibility Issues
Different API Standards: Each cloud platform uses different APIs, authentication methods, and data formats for security integration
Rate Limiting: Cloud providers implement different rate limiting policies that affect security tool integration
Permission Models: Varying identity and access management approaches across platforms complicate unified security monitoring
Data Export Limitations: Platform-specific restrictions on security data export prevent comprehensive cross-cloud analysis
Technical Barrier: Building integrations across multiple cloud platforms requires significant engineering effort and ongoing maintenance.
Data Sovereignty and Compliance
Regional Data Requirements: Different cloud platforms store data in different geographic regions, creating compliance complexity
Regulatory Variations: Cloud providers implement different approaches to regulatory compliance (GDPR, HIPAA, SOX)
Audit Trail Fragmentation: Compliance audits require correlating evidence across multiple platforms with different logging formats and retention policies
Data Residency: Organizations must track data location across multiple cloud providers to meet sovereignty requirements
Compliance Risk: Fragmented visibility across cloud platforms makes it difficult to demonstrate comprehensive compliance with data protection regulations.
Cost and Performance Optimization
Resource Allocation: Security monitoring consumes compute and network resources across multiple cloud platforms
Cost Optimization: Different pricing models and resource allocation strategies across cloud providers affect security tool costs
Performance Impact: Security monitoring tools must minimize performance impact across different cloud architectures and service models
Scalability: Security solutions must scale effectively across multiple cloud platforms with different auto-scaling behaviors
Economic Challenge: Managing security costs and performance across multiple cloud platforms requires sophisticated optimization strategies.
The Single Pane of Glass Advantage
Unified Data Visibility
Comprehensive Flow Tracking: Single platform that can follow data flows across AWS, Azure, Google Cloud, and SaaS applications
Cross-Platform Correlation: Ability to correlate security events and data movements across multiple cloud providers
Consistent Classification: Unified data classification and sensitivity labeling across all cloud platforms and applications
Complete Audit Trails: End-to-end visibility for compliance auditing across the entire multi-cloud environment
Security Benefit: Complete understanding of data security posture rather than fragmented platform-specific views.
Operational Efficiency
Single Dashboard: Unified interface for monitoring data security across all cloud platforms and applications
Consistent Alerting: Standardized alert formats and investigation procedures regardless of underlying cloud platform
Automated Correlation: Machine learning-based correlation of security events across multiple platforms
Unified Policy Management: Consistent security policies applied across all cloud platforms through a single interface
Productivity Gain: Security teams can operate more efficiently with unified tools rather than managing multiple platform-specific interfaces.
Risk Assessment and Management
Holistic Risk View: Complete understanding of data security risks across the entire multi-cloud environment
Cross-Platform Threat Detection: Ability to detect attack patterns that span multiple cloud platforms
Unified Compliance Reporting: Single source of truth for regulatory compliance across all cloud platforms
Comprehensive Impact Analysis: Understanding of business impact when security incidents affect multiple cloud platforms
Strategic Advantage: Better risk management decisions based on complete visibility rather than fragmented platform views.
Technical Architecture Requirements
Cloud-Agnostic Integration
Universal APIs: Integration capabilities that work across AWS, Azure, Google Cloud, and major SaaS platforms
Platform Abstraction: Ability to normalize data and security events from different cloud platforms into unified formats
Authentication Integration: Support for different identity and access management systems across cloud platforms
Network Connectivity: Secure connection capabilities across different cloud networking architectures
Technical Foundation: Architecture designed for multi-cloud environments rather than retrofitted single-platform tools.
Real-Time Cross-Cloud Processing
Stream Processing: Ability to process security events from multiple cloud platforms in real-time
Event Correlation: Machine learning capabilities to correlate events across different cloud platforms and identify multi-platform patterns
Low-Latency Response: Fast detection and response capabilities that work across cloud platform boundaries
Scalable Architecture: Processing capabilities that scale with multi-cloud data volumes and complexity
Performance Requirement: Real-time security monitoring across multiple cloud platforms without performance degradation.
Unified Data Models
Cross-Platform Data Schema: Standardized data models that work across different cloud platforms and services
Metadata Preservation: Maintaining data context and business purpose information as data moves between cloud platforms
Lineage Tracking: Complete data lineage across cloud platform boundaries with accurate timing and causality
Classification Consistency: Unified data classification that works consistently across all cloud platforms
Data Architecture: Comprehensive data model that supports multi-cloud complexity while maintaining simplicity for security operations.
Implementation Strategies
Assessment and Planning
Current State Analysis: Inventory existing cloud platforms, SaaS applications, and data flows across the multi-cloud environment
Integration Requirements: Identify specific integration needs for each cloud platform and application
Risk Prioritization: Focus initial implementation on highest-risk data flows and most critical cloud platforms
Resource Planning: Allocate sufficient resources for multi-cloud security tool implementation and ongoing management
Strategic Foundation: Comprehensive understanding of multi-cloud environment before implementing unified security solutions.
Phased Deployment
Phase 1: Implement unified visibility for most critical cloud platforms and data flows
Phase 2: Extend coverage to additional cloud platforms and SaaS applications
Phase 3: Enable advanced analytics and automated response capabilities across the complete multi-cloud environment
Phase 4: Optimize performance and cost across the unified multi-cloud security platform
Risk Management: Gradual implementation that maintains security coverage while building comprehensive multi-cloud capabilities.
Integration and Optimization
API Integration: Establish secure, reliable connections to all cloud platforms and major SaaS applications
Performance Tuning: Optimize security monitoring performance across different cloud architectures and service models
Cost Optimization: Balance security monitoring costs with performance and coverage requirements across cloud platforms
Team Training: Educate security teams on unified multi-cloud security operations and investigation procedures
Operational Excellence: Efficient multi-cloud security operations that leverage unified visibility capabilities.
The Business Case for Unified Multi-Cloud Security
Risk Reduction
Complete Visibility: Eliminate blind spots that exist when using platform-specific security tools
Faster Threat Detection: Identify multi-cloud attack patterns that single-platform tools cannot detect
Improved Compliance: Demonstrate comprehensive compliance across all cloud platforms and applications
Better Risk Assessment: Make informed decisions based on complete multi-cloud risk visibility
Security Value: Superior protection through comprehensive multi-cloud visibility and unified threat detection.
Operational Efficiency
Reduced Complexity: Manage multi-cloud security through unified interface rather than multiple platform-specific tools
Faster Investigation: Investigate security incidents across cloud platforms through single investigation workflow
Consistent Processes: Standardized security operations procedures across all cloud platforms
Team Productivity: Higher security team efficiency through unified tools and processes
Productivity Gain: Significant improvement in security operations efficiency through unified multi-cloud management.
Cost Optimization
Reduced Tool Sprawl: Consolidate multiple platform-specific security tools into unified solution
Lower Training Costs: Train security teams on single unified platform rather than multiple cloud-specific tools
Improved Resource Utilization: Optimize security monitoring resources across multiple cloud platforms
Better ROI: Higher return on security investment through comprehensive multi-cloud coverage
Economic Advantage: Better cost control and ROI through unified multi-cloud security platform.
The Multi-Cloud Security Future
Organizations cannot effectively secure multi-cloud environments with siloed, platform-specific security tools. The complexity will only increase as cloud adoption accelerates and organizations use more cloud platforms and SaaS applications.
Effective multi-cloud security requires Data Journeys™ approaches that provide:
- Unified visibility across AWS, Azure, Google Cloud, and SaaS applications
- Real-time cross-cloud data flow tracking and security monitoring
- Consistent security policies and compliance reporting across all platforms
- Comprehensive threat detection that works across cloud platform boundaries
The transition to unified multi-cloud security is essential for organizations operating in complex cloud environments. Siloed approaches will leave critical security gaps that expose organizations to threats and compliance violations.
Organizations implementing unified Data Journeys™ capabilities now will build competitive advantages through better multi-cloud visibility, more efficient security operations, and superior risk management across their entire cloud ecosystem.